With so many cybersecurity threats, businesses are grappling with the daunting task of protecting their digital assets. The rise in cloud-based operations and the proliferation of remote work have expanded the attack surface for potential breaches. To protect business from cyber attacks, Microsoft has developed two comprehensive security solutions known as Microsoft Defender for Cloud & Microsoft 365 Defender Suite (Defender for Office 365, Defender for Endpoint, Defender for Identity, Defender for Cloud Apps, and more). In this blog post, we will explore these powerful tools that provide robust protection for your organization’s cloud infrastructure.
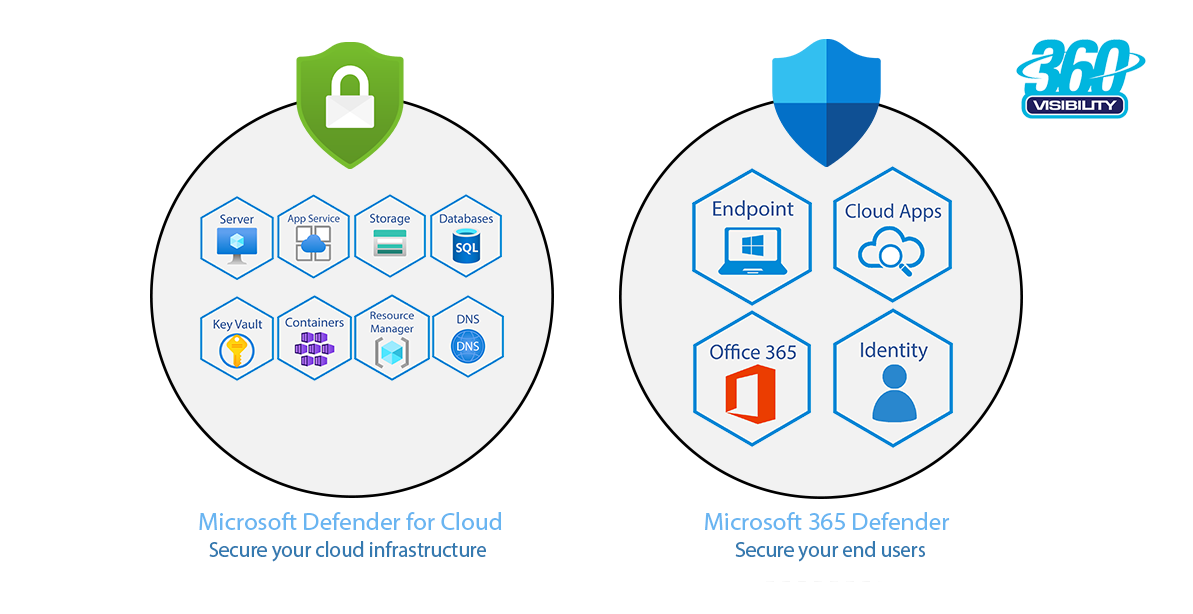
Defender for Cloud: Guarding Your Cloud Infrastructure
The cloud has become the backbone of modern business operations, offering scalability, accessibility, and flexibility. However, it also presents a prime target for cybercriminals. This is where Microsoft Defender for Cloud comes into play. Formerly known as Microsoft Azure Security Center, Defender for Cloud helps safeguard your cloud environment, providing real-time threat detection, advanced security recommendations, and threat surface reduction.
Discover our Managed Azure Cloud IT Services
Key Features of Defender for Cloud:
1. Threat Protection: With Defender for Cloud, you can gain visibility into potential threats across your cloud resources, including virtual machines, containers, storage accounts, and more. It leverages machine learning and behavioral analytics to detect and mitigate potential security risks proactively.
2. Adaptive Application Controls: Defender for Cloud uses machine learning to establish a baseline of normal application behavior, enabling it to detect and block malicious activities effectively. It employs automated whitelisting and intelligent recommendations to help you maintain control over your cloud environment without compromising security.
3. Compliance Monitoring: The solution offers continuous monitoring and assessments to ensure compliance with various industry regulations and best practices. It provides actionable recommendations and detailed reports, making it easier for your organization to meet regulatory requirements and maintain a robust security posture.
WATCH NOW: Getting Started with Microsoft Defender for Cloud
Are you concerned about the security of your Azure resources, but don’t know where to start?
Microsoft 365 Defender Suite: Protect Business From Cyber Attacks
In today’s digital landscape, organizations face an increasing number of sophisticated cyber threats that target various aspects of their operations. To address these evolving challenges, Microsoft offers the Microsoft 365 Defender Suite, a comprehensive security solution that brings together multiple powerful tools to protect your digital ecosystem. Let’s explore the key components of the suite: Defender for Office 365, Defender for Endpoint, Defender for Identity, and Defender for Cloud Apps.
Defender for Office 365
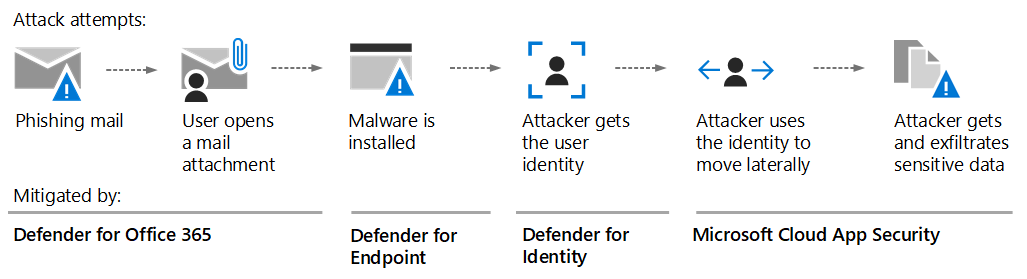
Microsoft Defender for Office 365 provides advanced threat protection for your organization’s email, collaboration tools, and productivity apps within the Microsoft 365 environment. It helps safeguard against phishing attempts, malware, malicious attachments, and other email-borne threats.
Key Features of Defender for Office 365:
- Advanced Threat Protection: Defender for Office 365 uses sophisticated algorithms and machine learning to detect and block advanced threats in emails, attachments, and links, minimizing the risk of successful phishing attacks and data breaches.
- Real-time Incident Response: The solution offers real-time visibility into security incidents, allowing security teams to investigate and respond swiftly to potential threats, ensuring the integrity of your email communication.
Defender for Endpoint
Microsoft Defender for Endpoint delivers comprehensive endpoint protection, threat detection, and response capabilities across various platforms, including Windows, macOS, Linux, Android, and iOS. It helps organizations defend against advanced attacks, secure devices, and proactively hunt for threats.
Key Features of Defender for Endpoint:
- Endpoint Protection: Defender for Endpoint provides real-time, multi-layered protection against malware, ransomware, and other malicious activities, using behavior-based analysis and machine learning models.
- Endpoint Detection and Response (EDR): The solution enables security teams to detect, investigate, and respond to sophisticated attacks, leveraging rich endpoint telemetry and advanced hunting capabilities.
- Vulnerability Management: Defender for Endpoint helps identify vulnerabilities and misconfigurations in endpoints, allowing organizations to prioritize and remediate security issues effectively.
Defender for Identity
Defender for Identity is designed to protect user identities and detect potential identity-based attacks in real-time. By analyzing user behaviors and leveraging AI, it helps identify and mitigate threats across on-premises and cloud environments.
Key Features of Defender for Identity:
- Identity Protection: Defender for Identity utilizes machine learning algorithms to establish a baseline of normal user behavior and detect anomalous activities that may indicate compromised accounts or insider threats.
- Threat Investigation and Response: The solution offers detailed insights into suspicious activities, allowing security teams to investigate potential identity-based threats and respond promptly to prevent unauthorized access or data breaches.
Defender for Cloud Apps
Defender for Cloud Apps provides security and compliance capabilities for cloud-based applications and services, including Microsoft 365 apps, collaboration platforms, and other SaaS applications. It helps protect against unauthorized access, data leaks, and malicious activities.
Key Features of Defender for Cloud Apps:
- Cloud App Security: Defender for Cloud Apps offers visibility into app usage, data sharing, and user activities, enabling organizations to enforce policies, detect anomalies, and mitigate risks across cloud-based applications.
- Data Loss Prevention (DLP): The solution helps organizations prevent sensitive data from being shared or leaked by identifying and classifying sensitive information, and enforcing policies to control data movement and sharing within cloud apps.
By leveraging the Microsoft 365 Defender Suite, organizations can benefit from a comprehensive security approach that covers email, endpoints, identities, and cloud applications. This holistic protection helps mitigate risks, detect advanced threats, and respond swiftly to security incidents, ensuring the integrity and resilience of your digital ecosystem.
KEEP READING: The Growing Dangers of Cyber Attacks and the Need for Cloud Security
Summary of Key Differences and Similarities between Defender for Cloud and Microsoft 365 Defender Suite:
What’s the difference between Defender for Cloud and Microsoft 365 Defender?
1. Scope: Defender for Cloud primarily focuses on securing the cloud infrastructure, providing protection for virtual machines, containers, storage accounts, and other resources within cloud environments. Microsoft 365 Defender Suite, on the other hand, offers a broader range of security capabilities, including email protection, endpoint security, identity protection, and cloud app security.
2. Integration: Defender for Cloud is a standalone solution that can be integrated with other security tools and services. In contrast, Microsoft 365 Defender Suite is an integrated suite that brings together multiple security components, offering a centralized management console and seamless integration across the suite.
3. Licensing: Defender for Cloud is licensed separately from Microsoft 365 Defender Suite. Organizations can choose to implement Defender for Cloud independently or as part of the broader suite, depending on their specific security needs.
How are Defender for Cloud and Microsoft 365 Defender the same?
1. Microsoft Defender Technology: Both Defender for Cloud and Microsoft 365 Defender Suite leverage the underlying Microsoft Defender technology to provide robust security capabilities. This technology includes machine learning, behavioral analytics, and threat intelligence to detect and mitigate potential security risks.
2. Real-time Threat Detection: Both solutions offer real-time threat detection capabilities, allowing organizations to identify and respond promptly to potential security incidents. They utilize advanced algorithms and analytics to detect and block threats across different layers of the digital ecosystem.
3. Proactive Incident Response: Both solutions provide proactive incident response capabilities, empowering security teams to investigate and respond swiftly to security alerts and potential breaches. They offer insights, recommendations, and tools to support efficient incident response and mitigation.
4. Centralized Management: Both Defender for Cloud and Microsoft 365 Defender Suite offer centralized management consoles, providing a unified view of the security landscape. These consoles enable security teams to monitor security events, manage alerts, and perform security-related tasks from a single interface.
Defender for Cloud and Microsoft 365 Defender Suite share similarities in terms of their real-time threat detection, proactive incident response capabilities, centralized management, and utilization of Microsoft Defender technology. However, they differ in scope and integration. Defender for Cloud focuses specifically on securing the cloud infrastructure, while Microsoft 365 Defender Suite offers a comprehensive suite of security components, including email protection, endpoint security, identity protection, and cloud app security. Organizations can evaluate their specific security requirements and choose the solution that best fits their needs, whether it be leveraging Defender for Cloud independently or implementing the broader Microsoft 365 Defender Suite for a comprehensive and integrated security approach.
When to Use Defender for Cloud versus Microsoft 365 Defender Suite
Choosing between Defender for Cloud and Microsoft 365 Defender Suite depends on your organization’s specific security needs and the extent of coverage required across your digital ecosystem. Here are some scenarios to consider when deciding which solution to use:
Use Defender for Cloud when:
- Cloud Infrastructure Protection: If your organization’s primary concern is securing cloud resources, such as virtual machines, containers, and storage accounts, Defender for Cloud is the ideal choice. It offers specialized features and recommendations tailored to cloud environments, providing real-time threat detection and proactive security measures for your cloud infrastructure.
- Independent Cloud Security Implementation: If your organization has already implemented security solutions for other aspects of your digital ecosystem (such as email, endpoints, or identity), and you specifically require robust cloud infrastructure protection, Defender for Cloud can be deployed as a standalone solution. This allows you to focus your resources and efforts on securing your cloud environment without duplicating security functionalities already covered by other solutions.
Use Microsoft 365 Defender Suite when:
- Comprehensive Digital Ecosystem Protection: If your organization requires a comprehensive security solution that covers multiple aspects of your digital ecosystem, including cloud infrastructure, email, endpoints, identity, and cloud applications, Microsoft 365 Defender Suite is the recommended choice. It provides a unified and integrated approach to security, ensuring consistent and comprehensive protection across various components.
- Seamless Integration and Centralized Management: If you prefer a centralized management console and seamless integration between different security components, Microsoft 365 Defender Suite offers a unified experience. It allows security teams to monitor, manage, and respond to security events from a single interface, streamlining operations and enhancing efficiency.
- Simplified Licensing and Cost Optimization: By opting for Microsoft 365 Defender Suite, organizations can benefit from consolidated licensing and cost optimization. Instead of purchasing and managing separate licenses for each security component, the suite offers a bundled licensing approach that can result in potential cost savings and simplified license management.
Example Scenarios:
1. Scenario: Cloud-First Organization
Company X is a cloud-first organization that heavily relies on cloud services for their operations. They host critical applications, store sensitive data, and use cloud infrastructure extensively. In this case, Defender for Cloud is the recommended choice. It provides specialized protection for the organization’s cloud resources, including virtual machines, containers, and storage accounts. With Defender for Cloud, Company X can proactively detect and mitigate threats specific to their cloud environment, ensuring the security of their cloud infrastructure.
2. Scenario: Comprehensive Digital Ecosystem Protection
Company Y is a mid-sized organization with a diverse digital ecosystem, including cloud services, email communication, endpoints, and user identities. They want comprehensive security coverage across their entire ecosystem to safeguard against a wide range of cyber threats. In this scenario, Microsoft 365 Defender Suite is the ideal solution. It offers a unified and integrated approach, providing protection for their cloud infrastructure with Defender for Cloud, email security with Defender for Office 365, endpoint protection with Defender for Endpoint, identity protection with Defender for Identity, and cloud app security with Defender for Cloud Apps. The suite ensures consistent and comprehensive security measures across all components of Company Y’s digital ecosystem.
3. Scenario: Existing Security Solutions in Place
Company Z already has robust security solutions in place for email, endpoints, and identity protection. However, they have identified the need to enhance security for their cloud infrastructure, which is hosted on Azure. In this case, Defender for Cloud can be implemented as a standalone solution. Company Z can leverage Defender for Cloud to focus specifically on securing their cloud resources, while their existing security solutions continue to cover other aspects of their digital ecosystem. By using Defender for Cloud independently, they can efficiently address their cloud infrastructure’s unique security requirements without duplicating functionalities already covered by their existing solutions.
4. Scenario: Centralized Security Management and Cost Optimization
Company W, a large enterprise, seeks centralized management and cost optimization for their security operations. They want a streamlined approach to manage security across their diverse digital ecosystem, including cloud infrastructure, email, endpoints, and identity. In this scenario, Microsoft 365 Defender Suite is the recommended choice. It offers a centralized management console, allowing Company W’s security teams to monitor, manage, and respond to security events from a single interface. Additionally, the suite provides consolidated licensing, simplifying license management and potentially resulting in cost savings for the organization.
By considering these example scenarios and evaluating your organization’s specific security requirements, you can make an informed decision on whether to use Defender for Cloud or implement the comprehensive Microsoft 365 Defender Suite to protect your digital ecosystem effectively.
It’s worth noting that organizations can also adopt a hybrid approach, leveraging both Defender for Cloud and Microsoft 365 Defender Suite based on their specific security requirements. For example, using Defender for Cloud to secure cloud infrastructure while implementing Microsoft 365 Defender Suite to cover other aspects of the digital ecosystem.
In summary, choose Defender for Cloud when your primary focus is securing your cloud infrastructure independently or when you have already implemented security solutions for other components of your digital ecosystem. Opt for Microsoft 365 Defender Suite when you require comprehensive protection across multiple areas and seek seamless integration, centralized management, and cost optimization. Evaluate your organization’s unique security needs to make an informed decision and create a robust security posture tailored to your specific requirements.
Importance of Defender for Cloud and Microsoft 365 Defender Suite to a Business: Operation, Financial, and Experience Perspectives
Defender for Cloud and Microsoft 365 Defender Suite offer crucial benefits to businesses, addressing security challenges and providing comprehensive protection for their digital ecosystem. Let’s explore the importance of these solutions from operational efficiency, financial stability, and enhanced user experience perspectives:
1. Operational Importance:
a. Protecting Critical Assets: Businesses heavily rely on cloud infrastructure, email communication, endpoints, and user identities to store, process, and access critical data. Implementing Defender for Cloud and Microsoft 365 Defender Suite ensures the protection of these assets from evolving cyber threats, reducing the risk of data breaches, downtime, and potential damage to the organization’s reputation.
b. Proactive Threat Detection and Response: Both solutions offer real-time threat detection capabilities, enabling businesses to identify and respond promptly to potential security incidents. By proactively detecting and mitigating threats, organizations can minimize the impact of attacks, prevent unauthorized access, and maintain operational continuity.
c. Streamlined Security Management: With Microsoft 365 Defender Suite, businesses benefit from centralized security management, providing a unified view of the digital ecosystem. This streamlined approach allows security teams to monitor, manage, and respond to security events efficiently, reducing complexity and enhancing operational efficiency.
2. Financial Importance:
a. Risk Mitigation: Implementing robust security measures, such as Defender for Cloud and Microsoft 365 Defender Suite, helps organizations mitigate financial risks associated with data breaches, cyberattacks, and non-compliance. By reducing the likelihood and impact of security incidents, businesses can avoid potential financial losses, legal expenses, and reputational damage.
b. Cost Optimization: Leveraging Defender for Cloud and Microsoft 365 Defender Suite can result in cost optimization. These solutions consolidate security functionalities and provide bundled licensing, simplifying license management and potentially reducing overall security costs. Additionally, by preventing security incidents and their associated financial consequences, organizations can achieve long-term cost savings.
3. Enhanced User Experience:
a. Trust and Confidence: Implementing robust security solutions like Defender for Cloud and Microsoft 365 Defender Suite instills trust and confidence among customers, partners, and stakeholders. Businesses that prioritize security demonstrate their commitment to protecting sensitive data and maintaining a secure environment. This trust builds long-term relationships, enhances brand reputation, and contributes to business growth.
b. Seamless and Secure User Interactions: Defender for Cloud and Microsoft 365 Defender Suite ensure a seamless and secure user experience by protecting email communication, endpoints, identities, and cloud applications. Employees can work without interruptions, knowing that their digital interactions are protected, enhancing overall productivity and job satisfaction.
c. Regulatory Compliance: Both solutions assist organizations in meeting regulatory and compliance requirements, such as GDPR, HIPAA, or industry-specific regulations. By complying with these standards, businesses maintain user privacy, protect sensitive data, and provide a positive user experience by adhering to legal and ethical obligations.
Defender for Cloud and Microsoft 365 Defender Suite are essential for businesses to ensure operational efficiency, financial stability, and enhanced user experience. By protecting critical assets, proactively detecting and responding to threats, streamlining security management, mitigating financial risks, optimizing costs, and building trust among users, these solutions contribute to the overall success and resilience of organizations in today’s cybersecurity landscape. Prioritizing the implementation of robust security measures with Defender for Cloud and Microsoft 365 Defender Suite establishes a strong security posture, safeguards digital assets, and fosters a positive business environment.
Conclusion:
Defender for Cloud and Microsoft 365 Defender Suite are powerful security solutions offered by Microsoft to address the diverse and evolving cybersecurity challenges faced by businesses today. While they share similarities in terms of real-time threat detection, proactive incident response, and leveraging Microsoft Defender technology, there are notable differences in scope and integration.
Defender for Cloud focuses on securing cloud infrastructure, providing specialized protection for virtual machines, containers, and storage accounts. It is suitable for organizations with a primary focus on securing their cloud resources independently or in combination with other security solutions.
On the other hand, Microsoft 365 Defender Suite offers a comprehensive and integrated approach to security. It covers various components of the digital ecosystem, including cloud infrastructure, email, endpoints, identity, and cloud applications. The suite provides centralized management, seamless integration, and cost optimization, making it suitable for organizations seeking comprehensive protection, streamlined operations, and consolidated licensing.
In terms of scenarios, organizations that heavily rely on cloud infrastructure can benefit from Defender for Cloud to ensure the security of their cloud resources. For those requiring comprehensive security coverage across multiple components of the digital ecosystem, Microsoft 365 Defender Suite offers a unified and integrated solution.
Key features of these solutions include advanced threat protection, real-time incident response, endpoint protection and detection capabilities, identity protection, cloud app security, vulnerability management, and compliance assistance. These features enable organizations to detect and mitigate threats, investigate security incidents, prioritize vulnerabilities, protect user identities, and ensure regulatory compliance.
In conclusion, both Defender for Cloud and Microsoft 365 Defender Suite provide businesses with robust security measures to protect their digital assets. By evaluating their specific security needs and considering the scenarios outlined, organizations can make informed decisions on which solution is best suited to their requirements. Whether focusing on cloud infrastructure or seeking comprehensive protection, implementing these solutions enables organizations to fortify their security posture, mitigate risks, and safeguard their digital ecosystem in an ever-evolving threat landscape.
Get Your Security Admin Report Today!
Are you concerned about the security of your organization’s digital landscape? Do you want to assess your current security posture and take actionable steps to strengthen your defenses? Look no further! Take advantage of our Azure Security Operations Report and Microsoft 365 Security Admin Report, which are designed to provide you with valuable insights into your current security state and guide you towards actionable next steps.
Why Choose Our Security Admin Reports?
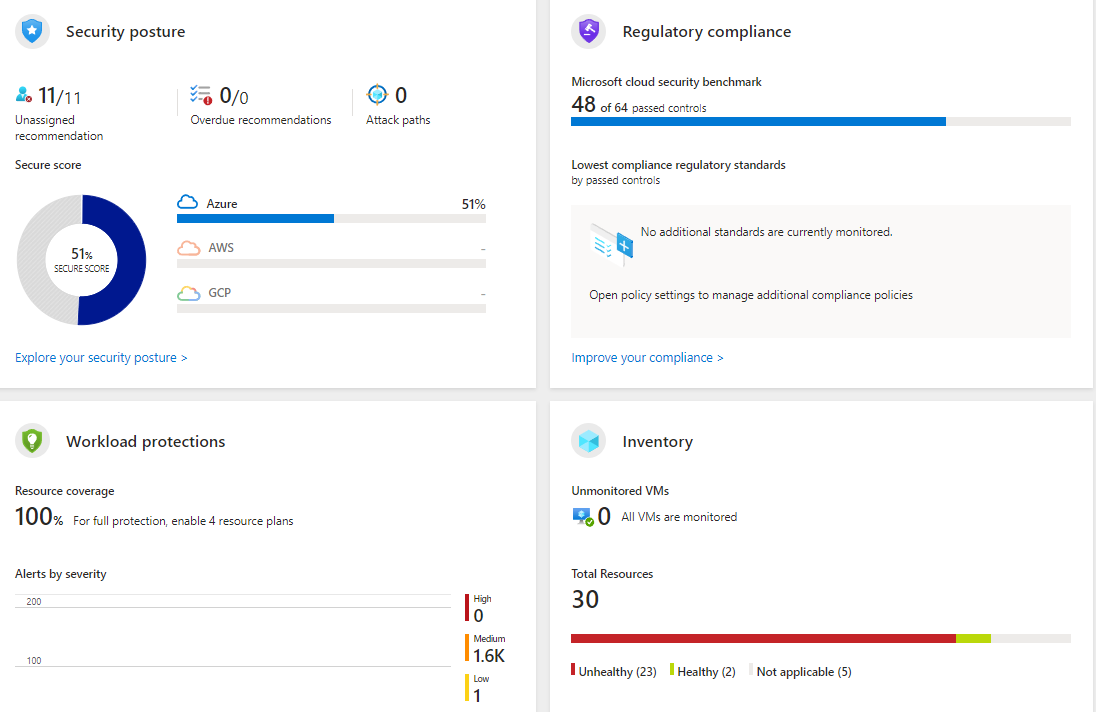
1. Comprehensive Assessment: Our report offers a holistic assessment of your organization’s security posture, covering both cloud infrastructure and Microsoft 365 (Endpoint, Identity, Cloud Apps, and Office 365). We analyze various factors, including threat detection, vulnerability management, compliance, and more, to provide you with a comprehensive overview of your current security state.
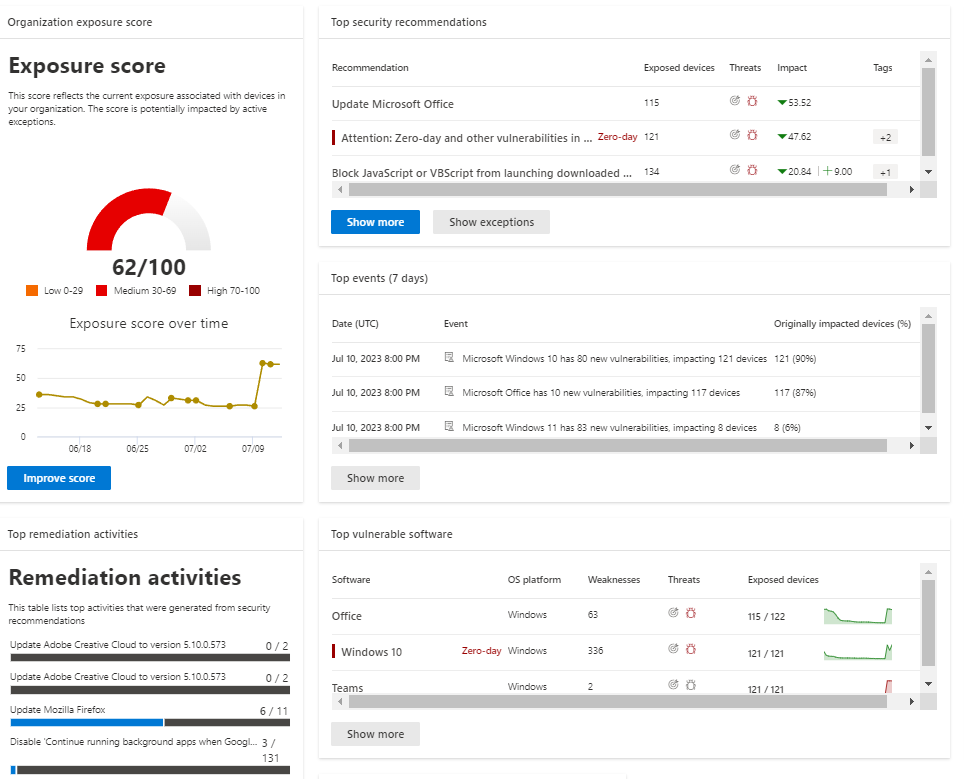
2. Actionable Next Steps: The report goes beyond just highlighting areas of improvement. It provides you with specific, actionable next steps tailored to your organization’s unique security needs. These recommendations are designed to help you prioritize your efforts and take proactive measures to enhance your security posture effectively.
3. Expert Insights and Best Practices: Our team of security experts has curated the report to incorporate industry best practices and the latest security trends. By leveraging their expertise, you can gain valuable insights and guidance on implementing robust security measures and staying ahead of emerging threats.
4. Measure Progress Over Time: Our Security Admin Report is not a one-time assessment. It serves as a benchmark for your organization’s security journey. By regularly reviewing and comparing your security scores over time, you can track your progress and ensure that you are continually improving your security posture.
How to Get Your Security Admin Report:
Getting your hands on your Security Admin Report is easy:
1. Contact our security team: Reach out to our dedicated security professionals to express your interest in the Security Admin Score Report.
2. Assessment and Data Collection: Our team will guide you through the assessment process, gathering the necessary data from your cloud infrastructure and endpoints to perform a thorough analysis of your security state.
3. Analysis and Report Generation: Our experts will analyze the collected data and generate a comprehensive Security Admin Report tailored to your organization. The report will include your current security score, areas of strength, vulnerabilities, and actionable next steps.
4. Review and Action: Once you receive the report, review the findings and recommendations carefully. Work closely with our team to prioritize and implement the actionable next steps to strengthen your security defenses effectively.
Take the First Step Towards Enhanced Security Today!
Don’t wait for a cyber incident to strike before taking action. Take control of your organization’s security by obtaining our Security Admin Report. Gain valuable insights into your current security state and receive actionable next steps to fortify your defenses. Together, we can ensure a robust security posture and protect your digital assets from evolving threats. Contact our security team today to get started on your security journey!



