Table of Contents
As businesses transition through growth and change, there’s a natural inclination to clean up operations. While it’s easy to tackle surface-level issues, vulnerability management digs deeper, uncovering hidden risks that threaten not just IT systems but the business as a whole. Microsoft Defender Vulnerability Management enhances this process by delivering asset visibility, intelligent assessments, and built-in remediation tools for Windows, macOS, Linux, Android, iOS, and network devices. By leveraging Microsoft threat intelligence, breach likelihood predictions, and device assessments, it rapidly and continuously prioritizes the biggest vulnerabilities on critical assets. Most importantly, it provides actionable security recommendations to mitigate risk.
What is Microsoft Defender Vulnerability Management?
Microsoft Defender Vulnerability Management identifies weaknesses within a system and mitigating the risks that arise from them. It’s not just about applying patches or updates to IT infrastructure; it’s about safeguarding the business from threats that can compromise operations, finances, and reputation.
Cyber-attacks are not only increasing in frequency but evolving in complexity. In fact, 60% of small businesses that experience a cyber attack go out of business within six months. The financial impact is also substantial, with cybercrime costing small and medium businesses over $2.2 million annually. This makes Microsoft Defender Vulnerability Management an important practice for any business. Without an effective strategy, your company becomes exposed to risks that go beyond the IT department and can affect customer trust, compliance, and even long-term profitability.
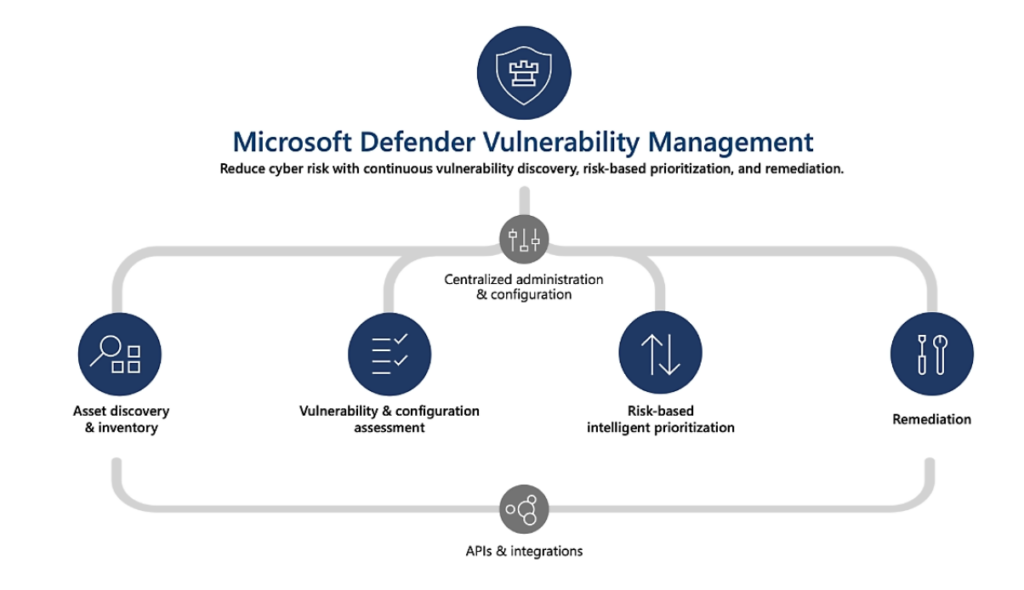
The Business Risks of Unaddressed Vulnerabilities
It’s easy to think of vulnerabilities as strictly an IT issue, but the repercussions can permeate every facet of an organization. A data breach or security failure can lead to:
- Operational Disruption: A vulnerability that allows a cyberattack to succeed can bring business operations to a halt. From supply chain disruptions to client services going offline, the impact can affect productivity and output.
- Financial Losses: The costs of a successful breach go beyond the need to just fix IT systems. Downtime, lost business, regulatory fines, and legal expenses add up quickly. For small and medium-sized businesses, these financial losses can be devastating.
- Damage to Reputation: Even a minor breach can result in lost customer trust. Rebuilding a damaged reputation takes years and often requires significant investment in public relations and customer retention strategies.
- Compliance Risks: Businesses in regulated industries face additional risks if they fail to protect sensitive data. Non-compliance with laws like GDPR or HIPAA can lead to substantial fines, not to mention the potential for lawsuits.
The Challenge of Closing Vulnerabilities on Your Own
Many businesses underestimate the complexity of Microsoft Defender Vulnerability Management and assume their internal IT teams can handle it. However, closing vulnerabilities is not a one-time fix—it’s an ongoing process that requires constant attention. Companies often face several challenges when managing vulnerabilities on their own, including:
- Resource Constraints: Smaller IT teams are already stretched thin managing day-to-day operations. Adding the responsibility of continuous vulnerability scanning, patching, and remediation can lead to burnout and overlooked issues.
- Evolving Threats: Cyber threats are constantly evolving, and new vulnerabilities are discovered almost daily. Keeping up with these emerging threats requires specialized expertise and up-to-date knowledge.
- Zero-Day Vulnerabilities: These vulnerabilities are unknown to the vendor and therefore have no immediate patch available. Identifying and mitigating zero-day vulnerabilities requires advanced tools and expertise that may not be available in-house.
- Integration Challenges: Many organizations use a variety of software that may not integrate smoothly with vulnerability scanning tools. This creates blind spots that leave the business exposed.
Attempting to address these challenges without expert guidance can lead to incomplete solutions, leaving critical vulnerabilities open to exploitation.

How Microsoft Defender Vulnerability Management Can Close the Gaps
As mentioned, Microsoft Defender Vulnerability Management not only identifies weaknesses but more importantly, it provides defenses for the potential risks that may arise by:
1) Continuous Threat Monitoring and Risk Assessment
Microsoft Defender Vulnerability Management continuously scans systems, applications, and network infrastructure to identify vulnerabilities in real time. It leverages built-in threat intelligence to assess risks associated with each vulnerability, helping prioritize and address the most critical issues. This proactive monitoring prevents vulnerabilities from being exploited by identifying weak points before they’re attacked.
2) Automated Remediation Recommendations and Actions
It provides tailored remediation recommendations, enabling security teams to address issues quickly. It also integrates with Microsoft Endpoint Manager, allowing for automated deployment of security patches or configuration adjustments to affected devices. This automation speeds up the vulnerability management process and reduces human error, which can help prevent new vulnerabilities from persisting in the network.
3) Comprehensive Visibility and Control Across Endpoints
With Microsoft Defender Vulnerability Management, IT teams gain visibility into the security posture of all endpoints, whether they’re on-premises or in the cloud. The tool supports attack surface reduction by applying security policies that mitigate vulnerabilities in application, network, and OS layers. This centralized visibility and control streamline response efforts, ensuring vulnerabilities are closed across diverse environments.
What’s more, other Microsoft solutions such as Azure, Dynamics 365, and Business Central play a pivotal role in addressing the challenges of vulnerability management. These platforms provide built-in security features, continuous updates, and real-time monitoring that help businesses stay ahead of emerging threats.
- Azure Security Center offers comprehensive threat protection and automated threat detection, ensuring that vulnerabilities are identified and addressed before they can impact operations.
- Microsoft 365 provides cloud-based security tools like advanced threat protection, data loss prevention, and multifactor authentication, which help secure both data and access points.
- Business Central integrates financial, operational, and customer data into one secure platform, ensuring that all business processes are protected and streamlined, reducing risks from disjointed systems.
Advanced Security is Not a Luxury — It’s a Necessity
Protect your business with our Microsoft 365 Advanced Security and learn more about the benefits of Microsoft Defender Vulnerability Management. Our solutions are designed for businesses demanding the latest and most advanced security offerings, ensuring your organization stays resilient.
What’s included:
- Initial Security Assessment: Start with a solid foundation. Our experts conduct a comprehensive audit to understand your current security posture; identify vulnerabilities; uncover risks; and provide actionable insights.
- Quarterly Review: Stay ahead of threats with quarterly security report reviews and status meetings. Plus, we share the latest security trends and suggest adjustments to strategies for maximum protection.
- Monthly Action Items: Consistency is key. Each month, we’ll update your security measures and identify new areas of improvement. We’ll communicate action items; review tasks; and provide progress updates
Contact us to learn more about how we can work together to protect your business with Microsoft Defender Vulnerability Management.



