A Cloud Access Security Broker (CASB) is software that sits between users and cloud applications, and monitors all activity and enforces security policies. Microsoft’s CASB product, Microsoft Cloud App Security (MCAS) is that and more. We will go through a few sample scenarios and understand how MCAS provides insight in each of these situations.
Identify Extent of Data Breach
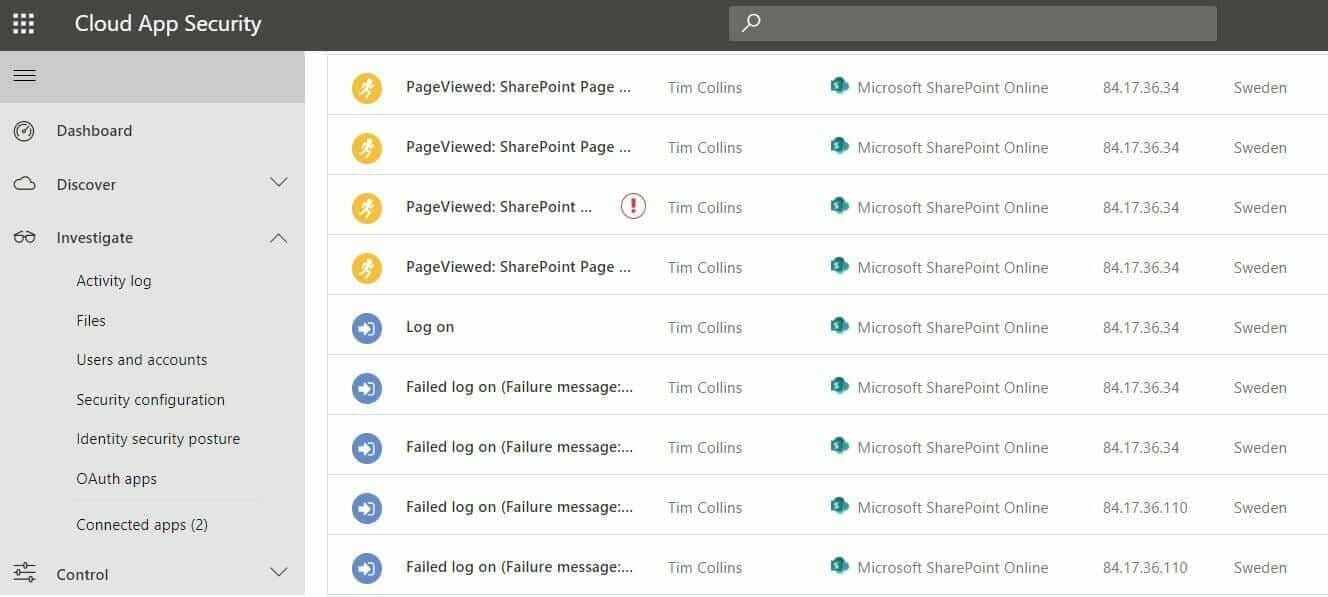
The one user who was yet to implement MFA gets compromised by a common password spray attack. At this point, you would like to know what resources the hacker accessed using the compromised account. The following screenshot shows in detail on how the hacker after a few attempts was able to successfully login and access SharePoint data that the user had access to. With this insight, you will be able to understand the level of data breach that has taken place and take next steps accordingly.
Get Alerted to Data Exfiltration
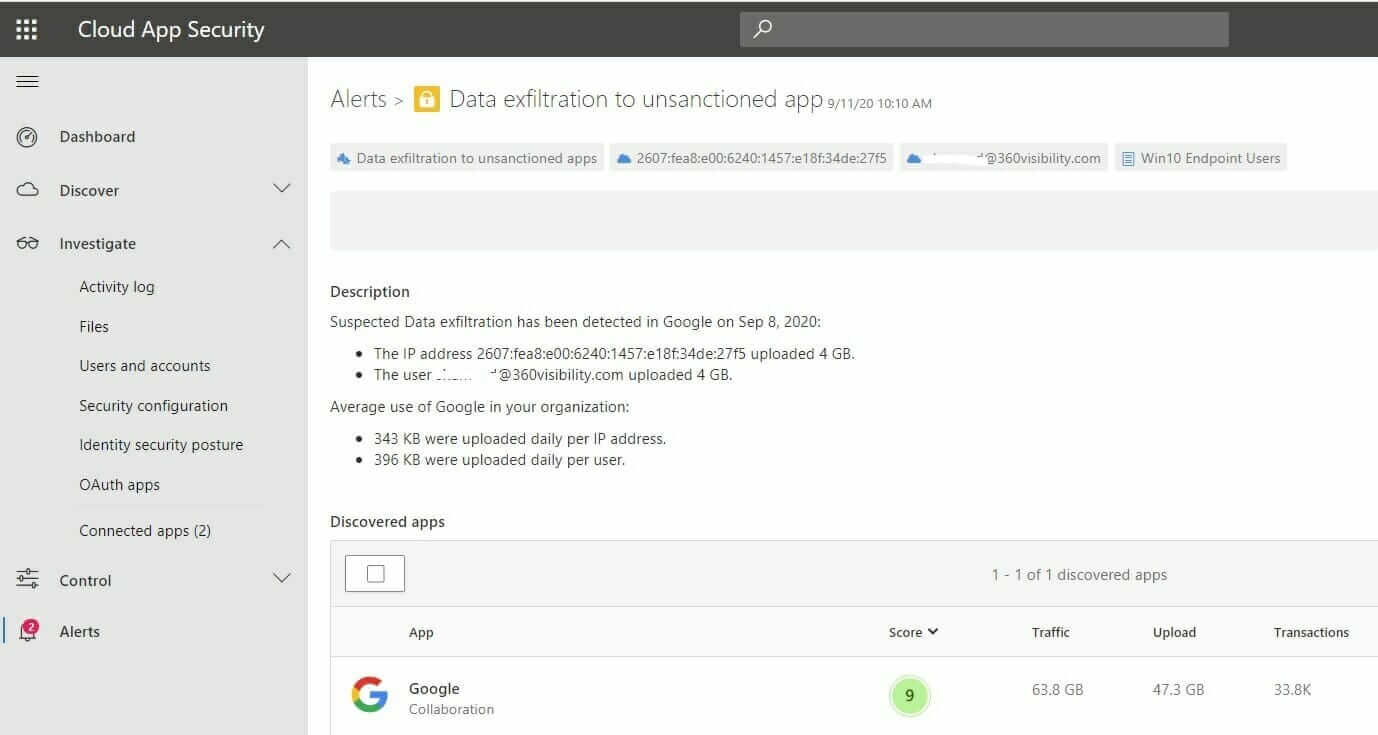
Intellectual property / Corporate data is the most valuable asset for an organization. As seen in the screenshot below, MCAS can detect when data is being exfiltrated and alert you with detailed information.
Analyze OAuth App Permissions
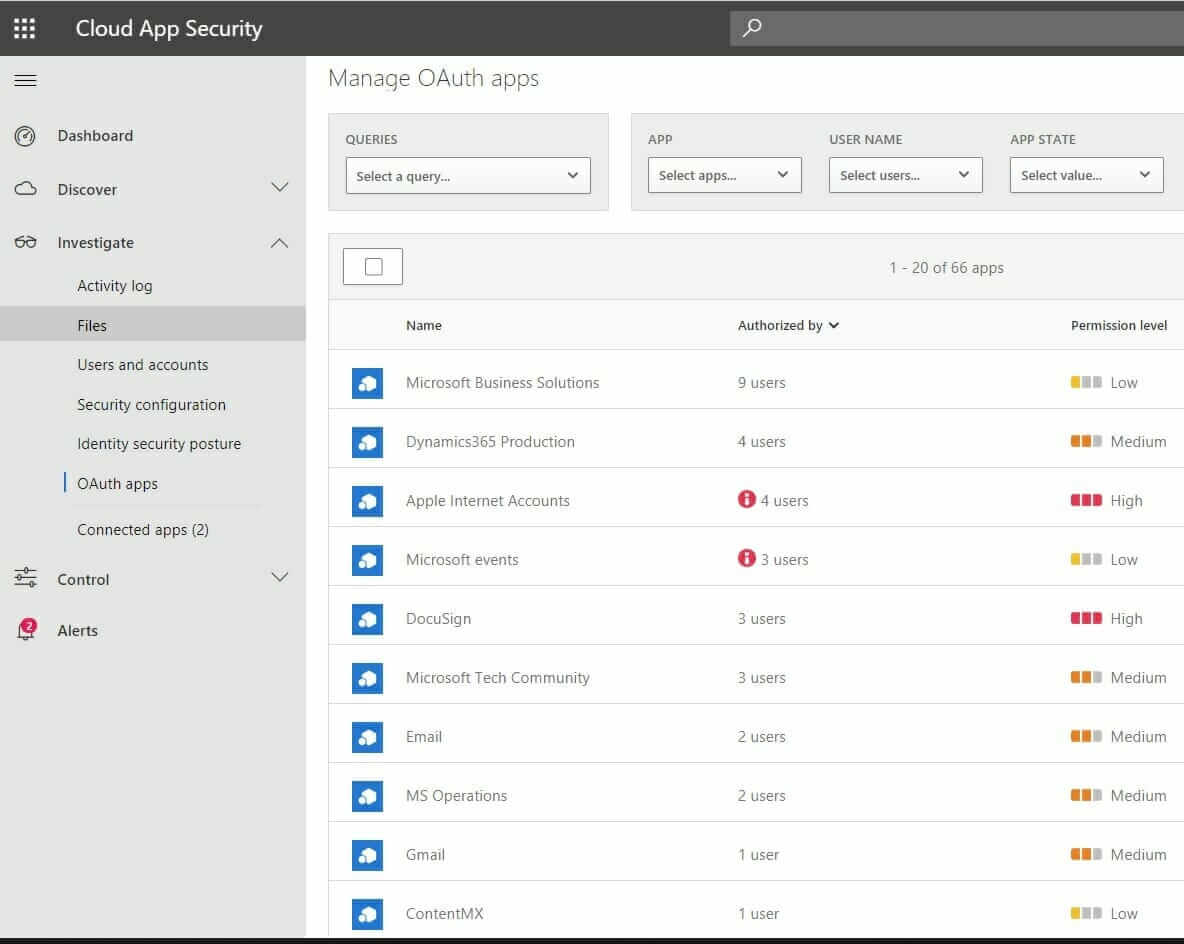
Let’s say you have implemented multi-factor authentication across your organization, blocked basic/legacy authentication use and also hardened your endpoint security. Sophisticated hacker groups are aware of this and use OAuth apps to get users to grant access to their user accounts and mailbox data without sharing credentials. Do note that there might be legitimate use cases such as the Calendly OAuth app requesting access to an user’s calendar to help schedule meetings. With MCAS, you can gain insight and check each of the OAuth app’s access level and choose to either sanction it or block it.
Improve Identity Security Posture
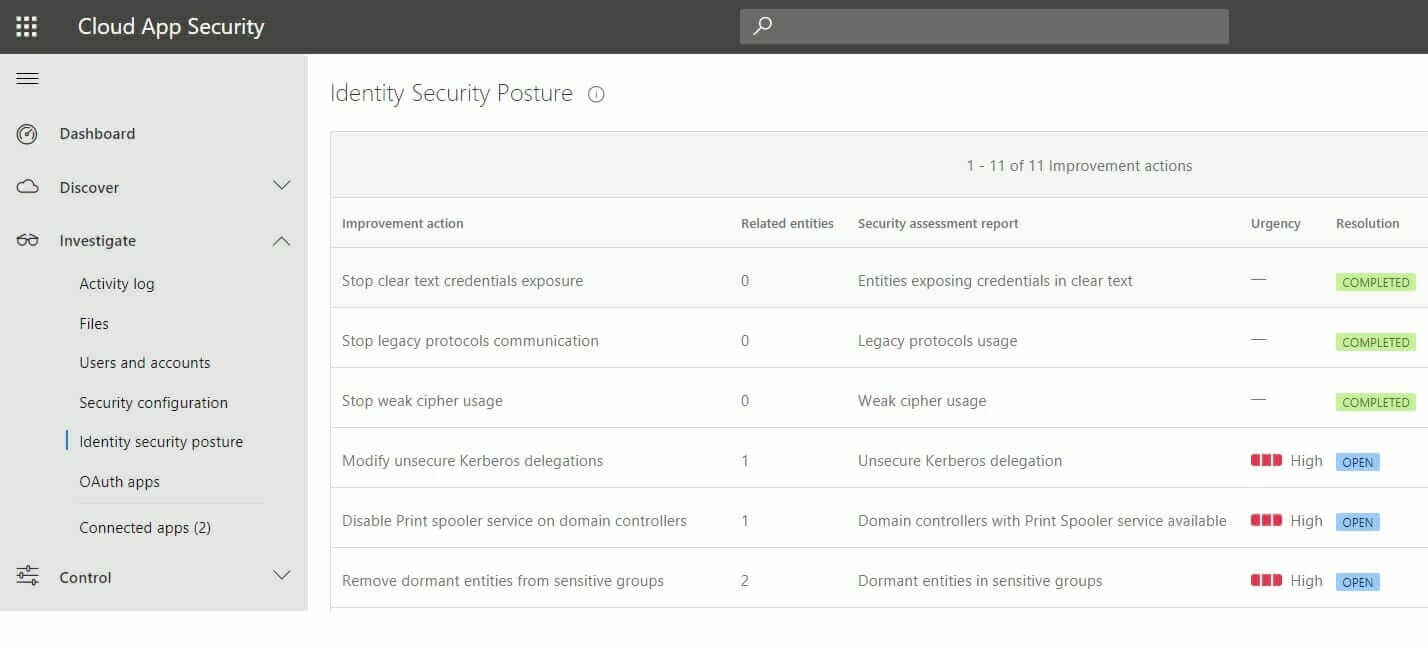
You have a hybrid identity solution wherein your on-premises AD users are synchronized with Azure AD. You also have the Microsoft Defender for Cloud and Microsoft 365 Defender solution implemented in your on-premises network to identify and detect threats in your corporate network. Leveraging MCAS, you can not only get alerted to malicious activity in your network but also take proactive steps to increase your identity security posture based on signals provided by Azure ATP to MCAS. The below screenshot provides a sample insight into where your identity security posture is at your corporate network. For example, any multi-function printer that uses AD for address book but is not configured to use SSL for authentication will trigger a “Stop clear text credentials exposure” improvement action. Another example is a temporary domain admin account that was used for a project some time ago but isn’t being used anymore will trigger a “Remove dormant entities from sensitive groups” improvement action. These improvement actions will not only show what the issue is but also pinpoint the user or device that the action needs to be taken on.
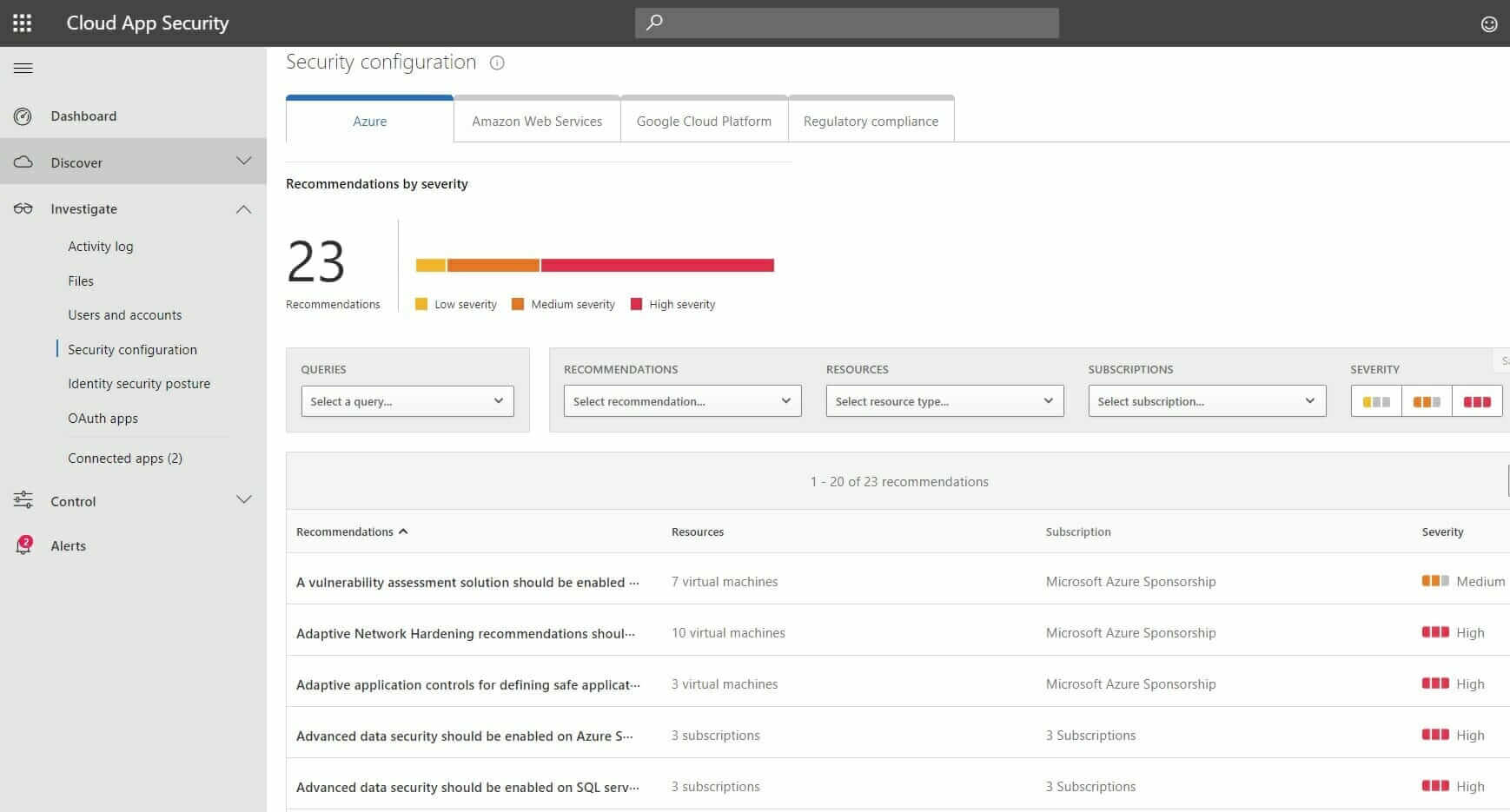
Assess Cloud Infrastructure Security Configuration
With an API connector to your Cloud Infrastructure be it AWS, Azure or GCP, you will be able to identify your existing security configuration and take necessary steps to secure the workloads as seen in the screenshot below.
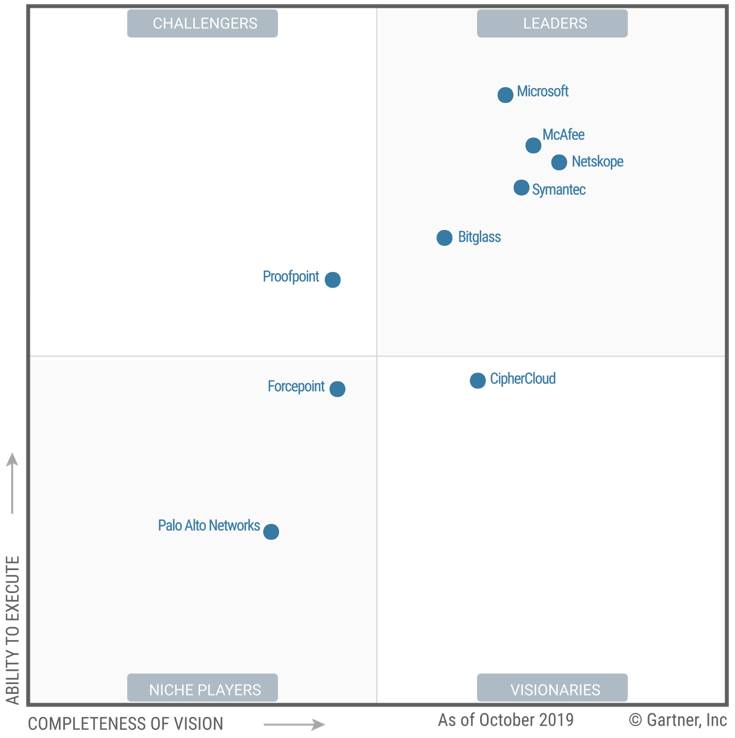
Recognized by Gartner as a leader in the CASB market, the Microsoft Cloud App Security (MCAS) solution is indeed a powerful and versatile solution.
360 Visibility regularly conducts Cloud Security assessments for organizations to identify their current security posture and help implement security best practices using Microsoft tools. Contact us today to schedule a Cloud Security Assessment and Workshop tailored to your unique environment and begin implementing the security tools and increasing your security posture.



