Organizations are trending towards remote jobs and this year there are more than any year previously. This relies on all their data being online and allowing workers to access it anywhere from any device. However, cyber threats are also the highest they’ve ever been requiring organizations to have the most accessible and secure data.
Related Article: A Crash Course in Azure Active Directory and Unified Identity and Access Management (IAM)
Malicious hackers have devised many ways to acquire passwords and steal data. In fact, 81% of all hacking- related security breaches originate from stolen passwords. There are many ways hackers try to acquire data. Phishing is one of the most common. The hacker will call or email the target with a compelling message that requires them to enter private information. This could be an email disguised as a common website where the user needs to enter their log in information. This method is done in bulk sending hundreds or thousands of emails trying to catch as many people as possible. Spear Phishing is another common method and is aimed at a smaller group of people. This method requires the hacker to research information on the target or the company they work for. These messages will include details about their work, coworkers, or personal information to make the target believe the sender is more credible than they are. 95% of successful phishing attacks lead to some form of malicious software installation.
High risk levels are amplified by users’ risky password habits
- 75% of users use the same password for social networking and email
- 71% of accounts are guarded by passwords used across multiple sites, and 46% of users employ a password that is at least five years old
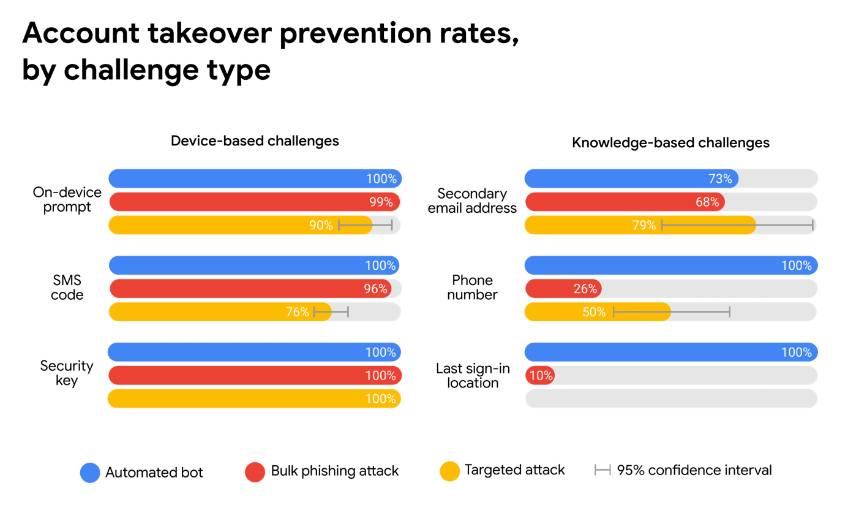
How do you combat this and keep your company safe?
Using Microsoft 365 you can prevent, manage, and respond to threats. You can safeguard users’ identities to prevent them being abused. You can detect and respond to identity-based threats quickly and effectively by managing cloud activity. With the implementation of a two-factor authentication process (multi-factor authentication). you can prevent an attack even if the hacker has your password. In fact, multi-factor authentication blocks 100% of automated bot attacks.
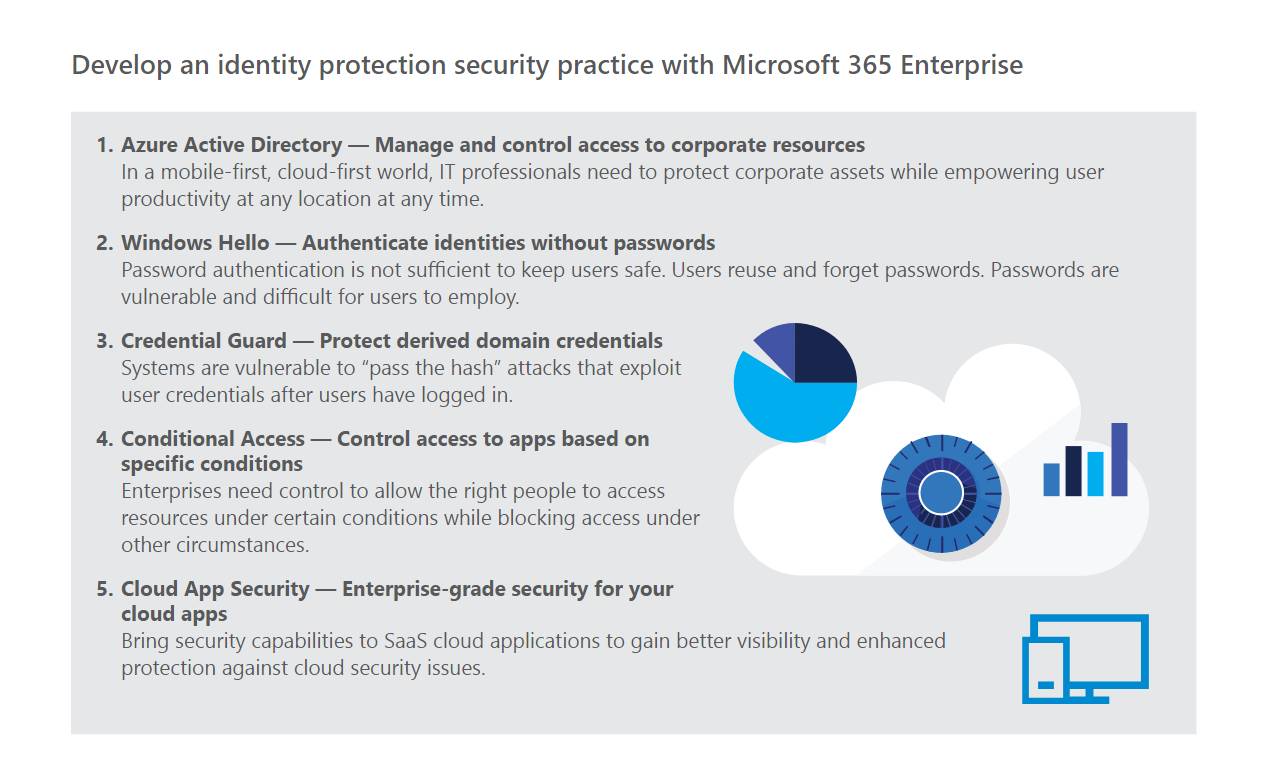
Working with a Microsoft Cloud Solution Provider that understands cloud cyber security and your business is critical to deploying and managing a cloud security governance policy that is respected and adhered organization-wide along with a system to automate threat protection.
360 Visibility’s Cloud Cyber Security team is at the forefront of deploying and integrating Microsoft’s advanced threat protection and security protocols for your company’s data, staff, and workloads, and understand the critical elements to work with you to develop cloud security policies to safeguard your operations.
Contact 360 Visibility to speak with our Cloud Cyber Security team. We will work with you so that your technology and staff adopt security best practices, ensuring your business is protected from potential cloud security threats.


